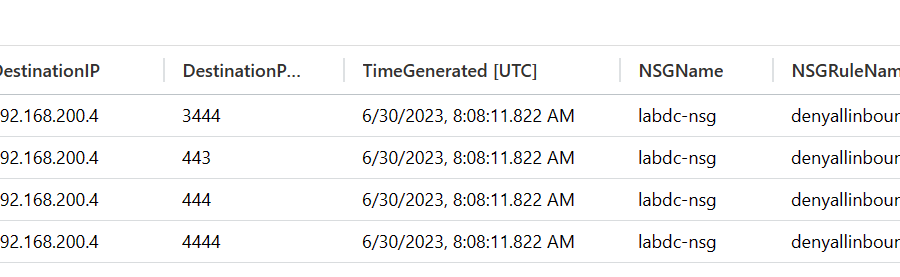
Azure Network Security Groups (NSGs) actively function as access control devices, effectively filtering network traffic within an Azure virtual network. By specifying the source and destination, port, and protocol, NSGs ensure secure communication between Azure resources. Moreover, NSGs offer a valuable feature: they can generate NSG flow logs, providing essential information about the IP traffic flowing through the network security group. These logs are instantly injected into a designated Storage Account, enabling administrators to conveniently review them as text files.
While text-based logs offer vital insights, Microsoft Azure takes it a step further by providing Log Analytics, a powerful tool that allows administrators to visualize NSG flow logs. By leveraging Log Analytics, administrators can gain a comprehensive understanding of network traffic patterns and potential security risks. However, it’s worth noting that Log Analytics has a slight drawback—the polling of logs from the Storage Account occurs every 10 minutes. Therefore, for instant log review, direct access to the storage account is necessary to obtain the most up-to-date information.
Enabling NSG Flow Logs in Log Analytics involves a two-step process. Firstly, you need to create a flow log and traffic analytics workspace. Detailed instructions for setting up flow logs for a single NSG can be found in this Microsoft documentation: https://learn.microsoft.com/en-us/azure/network-watcher/nsg-flow-logging#create-a-flow-log-and-traffic-analytics-workspace. Additionally, if you want to deploy NSG flow logs across multiple NSGs using Azure Policy, refer to this guide: Manage NSG flow logs using Azure Policy – Azure Network Watcher | Microsoft Learn. These resources offer step-by-step instructions to configure NSG Flow Logs according to your specific requirements.
Once NSG Flow Logs are enabled and actively collecting data, accessing and analyzing the logs becomes crucial. To view the logs, navigate to the Log Analytics Workspace, where you’ll find a built-in query named “IPv4 NSF Flow Log Search.” This pre-configured query streamlines the log analysis process, allowing you to efficiently retrieve and examine relevant log data. By utilizing this query, you can filter and manipulate the logs to extract valuable insights on network traffic patterns, potential security incidents, or any other specific information of interest.
Examples
Let’s see some custom queries to narrow down the results based on the needs.
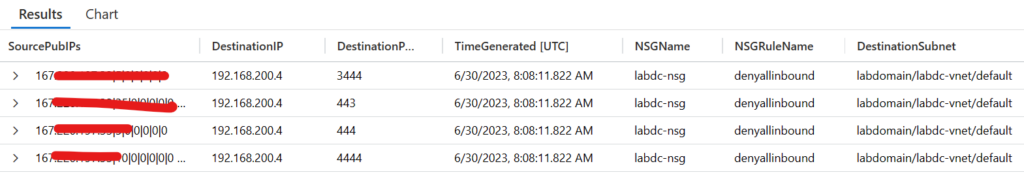
Search all traffic from a Public IP against a Network Security Group:
AzureNetworkAnalytics_CL | extend NSGRuleAction=split(NSGRules_s,'|',3)[0] | extend NSGRuleName=tostring(split(NSGRules_s,'|',1)[0]) | extend NSGName=tostring(split(NSGList_s,'/',2)[0]) | where NSGName == "labdc-nsg" | where SrcPublicIPs_s contains "167.2XX.XX.XX" | summarize count() by SourcePubIPs=SrcPublicIPs_s, SourceIP=SrcIP_s, DestinationIP=DestIP_s, DestinationPort=DestPort_d, TimeGenerated, NSGName, NSGRuleName, SourceSubnet=Subnet1_s, DestinationSubnet=Subnet2_s
Results:
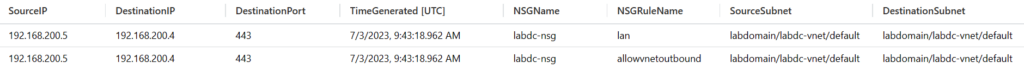
Search for internal traffic between two VMs:
AzureNetworkAnalytics_CL | extend NSGRuleAction=split(NSGRules_s,'|',3)[0] | extend NSGRuleName=tostring(split(NSGRules_s,'|',1)[0]) | extend NSGName=tostring(split(NSGList_s,'/',2)[0]) | where NSGName == "labdc-nsg" | where DestIP_s == "192.168.200.4" and SrcIP_s == "192.168.200.5" | summarize count() by SourcePubIPs=SrcPublicIPs_s, SourceIP=SrcIP_s, DestinationIP=DestIP_s, DestinationPort=DestPort_d, TimeGenerated, NSGName, NSGRuleName, SourceSubnet=Subnet1_s, DestinationSubnet=Subnet2_s
Results:
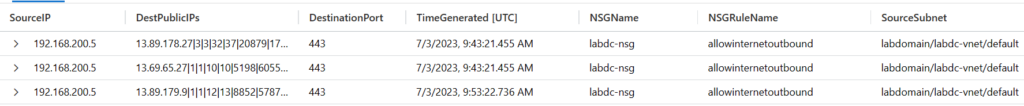
Search for traffic from internal IP to a public destination:
AzureNetworkAnalytics_CL | extend NSGRuleAction=split(NSGRules_s,'|',3)[0] | extend NSGRuleName=tostring(split(NSGRules_s,'|',1)[0]) | extend NSGName=tostring(split(NSGList_s,'/',2)[0]) | where NSGName == "labdc-nsg" | where SrcIP_s == "192.168.200.5" | summarize count() by SourcePubIPs=SrcPublicIPs_s, SourceIP=SrcIP_s, DestPublicIPs=DestPublicIPs_s, DestinationPort=DestPort_d, TimeGenerated, NSGName, NSGRuleName, SourceSubnet=Subnet1_s, DestinationSubnet=Subnet2_s
Results:
In summary, Azure Network Security Groups serve as powerful access control devices for regulating network traffic within an Azure virtual network. The inclusion of NSG flow logs and Log Analytics enhances administrators’ visibility and understanding of network activity. By following the necessary steps to enable NSG Flow Logs and leveraging the Log Analytics Workspace, you can effectively monitor and analyze network traffic data, thereby improving the security and performance of your Azure resources.

Pantelis Apostolidis is a Sr. Specialist, Azure at Microsoft and a former Microsoft Azure MVP. For the last 20 years, Pantelis has been involved to major cloud projects in Greece and abroad, helping companies to adopt and deploy cloud technologies, driving business value. He is entitled to a lot of Microsoft Expert Certifications, demonstrating his proven experience in delivering high quality solutions. He is an author, blogger and he is acting as a spokesperson for conferences, workshops and webinars. He is also an active member of several communities as a moderator in azureheads.gr and autoexec.gr. Follow him on Twitter @papostolidis.