Create an Ultra High Available on-prem <-> Azure VPN Connection
At this post we will see how to make a high available connection between our on-premises network and Azure. This way we will have an Active-Active Dual-Redundancy VPN Connection.
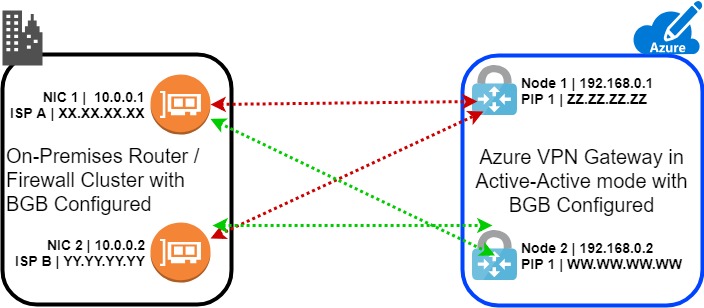
The idea behind this is that we have a router/firewall cluster,connected with two ISPs and we want to also have a VPN connection with Azure using both ISPs actively. I call this an end-to-end high available connectivity between our on-premises infrastructure and Azure. Actually the active-active dual redundant connections needs to have two different on-premises VPN devices, but we can accomplish almost the same functionality with one device and two different interfaces with two different ISPs.

The requirement for this topology, except the router/firewall cluster and the two ISPs is that the Azure VPN Gateway must be Standard or HighPerformance SKU. The Basic SKU does not support Active-Active mode.
As you can see at the above diagram, the Active-Active VPN Gateway created two Active VPN Nodes. The connection of each node to each on-premises network interface in a mesh topology. All network traffic is distributed through all the connections. In order to accomplish this connectivity we need to also enable BGP to both on-premises device and Azure VPN Gateway with different ASN.
Lets lab it:
Create a Virtual Network Gateway, VPN, Route Based and SKU VpnGw1 or larger
Enable active-active mode, this will create two nodes, and give the names of the two Public IPs.
Check the Configure BGB ASN and change the default ASN, I used 65510
wait a lot… more than the typical 45 minutes, a lot more…

When the gateway is created you will see that the public ip address is called “First public IP address”. If you click the “see more” link you will see the second IP too.

You can see both IP form the Properties page too.

Second we need to create two Local network Gateways, to represent the two interfaces of our on-premises device. Both must be created with the same ASN. This ASM must be different than the Gateways’ and this ASN must be configured at the configuration of the local devices VPN connection.
 ]
]
Now, create the connection

And remember to enable BGP at the Connection’s Configuration

As soon as the local device is configured both connections became connected.

From powershell we can see both local IPs of the two nodes of the Azure VPN Gateway,

Test and Troubleshooting
Currently the only way to see the connections between the Azure Gateway Nodes and the local devices interfaces is the below powershell command
Get-AzureRmVirtualNetworkGatewayBGpPeerStatus -VirtualNetworkGatewayName “gatewayname” -ResourceGroup “resourcegroupname”

Every time you run this command you get answer from one of the two nodes at random. At the above screenshot, first is one node and second is the other.
The first node’s peer, 192.168.xx.9 shows that is connected to the 10.xx.xx.2 local network’s peer and connecting at the second peer 10.xx.xx.1
The second node’s peer, 192.168.xx.8 shows that is connected to the 10.xx.xx.1 local network’s peer and connecting at the second peer 10.xx.xx.2

The test I performed was to unplug one interface from the local device. The azure gateway’s first node State was both Connecting and the second node was the same, connecting to .2 and connected to .1. At this test I did lost a single ping.
After that I plugged the cable back, waited less than a minute and unplugged the second cable. Now the first node shows still disconnected but the first node connected to the .2 local IP and connecting to .1. With this test I lost only one ping. Also I realized that it is random which node’s private IP will connect with the local device’s private IP. Both Azure Gateway’s IPs 192.168.x.8 & 9 can connect with the local device’s IP 10.x.x.1 & 2 and this is the magic of the Active-Active Dual Redundancy VPN connection.

Pantelis Apostolidis is a Sr. Specialist, Azure at Microsoft and a former Microsoft Azure MVP. For the last 20 years, Pantelis has been involved to major cloud projects in Greece and abroad, helping companies to adopt and deploy cloud technologies, driving business value. He is entitled to a lot of Microsoft Expert Certifications, demonstrating his proven experience in delivering high quality solutions. He is an author, blogger and he is acting as a spokesperson for conferences, workshops and webinars. He is also an active member of several communities as a moderator in azureheads.gr and autoexec.gr. Follow him on Twitter @papostolidis.

If I wanted to add more than two connections to the vpn gateway would I have to have another vpn gateway object? thank you very much for sharing this lab i want to implement it in three different locations i think i have to use three vpn gateway.
Hi Gerson,
the VPN Gateway is a Regional resource. Suppose you want to connect to more than one Region, etc. West Europe, and North Europe, you need two VPN Gateways. One VPN Gateway is in West Europe and another one in North Europe.
A single VPN Gateway can have multiple connections. This means you can have multiple connections from multiple locations to a single VPN Gateway. e.g. You have a VPN Gateway in West Europe. You can connect from multiple locations to this VPN Gateway.
HI Pantelis,
Good posted.
1. In this active/active both on-prem device connect to the same IP address (192.168.0.2)?
2. If i did not want to use active/active, use active/standby, not enable active/active feature.
if i create one VPN GW with one ip, and 2 Local network gateway, connecting to two differnet ip address of each on-prem device.
do each on-prem devices connect do the same one ip address of on VPN GW