Network security policies are a very handy feature when you use Private Endpoints on Azure. If you enable network security policies for User-Defined Routes, the /32 routes that are generated by the private endpoint and propagated to all the subnets in its own VNet and directly peered VNets will be invalidated if you have User-Defined Routing, which is useful if you want all traffic (including traffic addressed to the private endpoint) to go through a firewall, since otherwise, the /32 route would bypass any other route.
By default, network policies are disabled for a subnet in a virtual network and you need to enable it manually, from the Azure Portal after the VNET creation, or you need to specify it in your script if you are deploying with PowerShell, Cli, Bicep or any other IaC.
To ensure that Network security policies are enabled, and force enable it, we can use an Azure Policy. The below Azure Policy checks if the Network security policies are enabled, and if not it automatically enables it. The result of this policy is:
- for new Virtual Networks, it automatically enables Network security policies to all subnets, even if you forgot to select it upon the creation
- for existing virtual Network subnets, it uses a remediation plan to evaluate and enable the Network security policies.
The Policy:
{
"mode": "All",
"policyRule": {
"if": {
"field": "Microsoft.Network/virtualNetworks/subnets[*].privateEndpointNetworkPolicies",
"notEquals": "Enabled"
},
"then": {
"effect": "modify",
"details": {
"roleDefinitionIds": [
"/providers/Microsoft.Authorization/roleDefinitions/4d97b98b-1d4f-4787-a291-c67834d212e7"
],
"operations": [
{
"operation": "addOrReplace",
"field": "Microsoft.Network/virtualNetworks/subnets[*].privateEndpointNetworkPolicies",
"value": "Enabled"
}
]
}
}
},
"parameters": {}
}
To add the Policy to your Azure environment:
- Go to the Azure Policy Definitions blade (shortcut: Policy – Microsoft Azure )
- Add Policy Definition
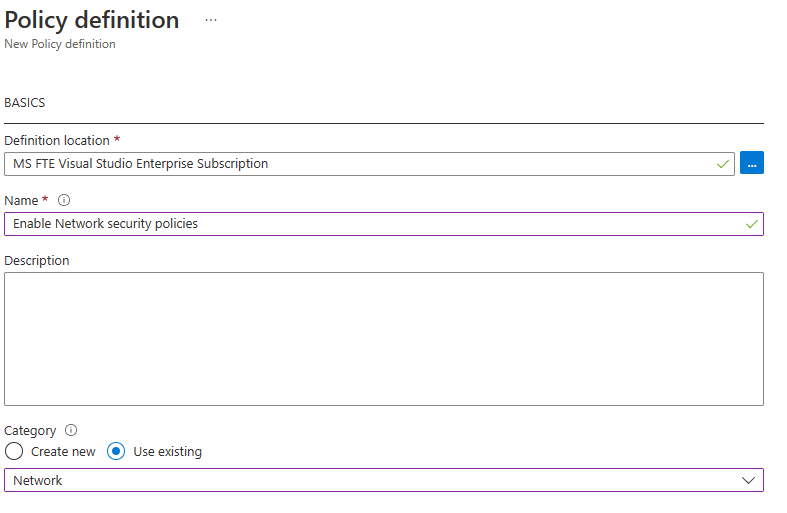
- Provide a location (subscription) to save the policy object, and give a name and a category. Use the existing Network category.
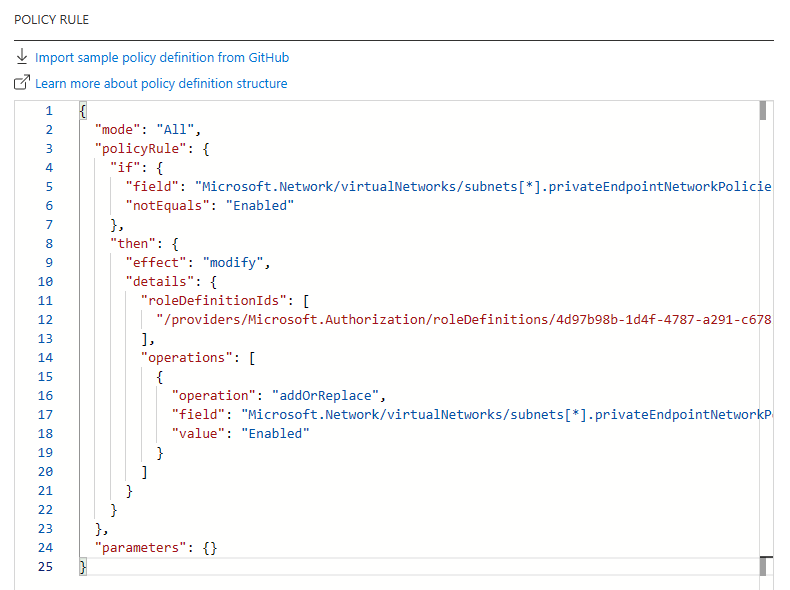
- Paste the policy Json
- Select a Role Assignment. You need a role that will have editor access to the subnet. For my demo, I used the Network Contributor build-in role (4d97b98b-1d4f-4787-a291-c67834d212e7) for the action.
- Once the Policy is created, open it and you need to assign it to a scope (MG, Subscription, Resource Group)
- Assign the policy to the scope you want, like Management Group, Subscription, or Resource Group and one thing that needs attention is to create a remediation task and a Managed Identity.
- The remediation task is needed to remediate the existing resources and the Managed Identity for the modification action.
The Policy is in Audit only mode, in case you just need to audit if there are any subnets that don’t have privateEndpointNetworkPolicies enabled.
{
"mode": "All",
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Network/virtualNetworks/subnets"
},
{
"field": "Microsoft.Network/virtualNetworks/subnets[*].privateEndpointNetworkPolicies",
"notEquals": "Enabled"
}
]
},
"then": {
"effect": "audit"
}
},
"parameters": {}
}
You can get the Policy Json files at my Github repo: https://github.com/proximagr/automation#policy-audit—enable-network-policy-for-private-endpoints-blog-post

Pantelis Apostolidis is a Sr. Specialist, Azure at Microsoft and a former Microsoft Azure MVP. For the last 20 years, Pantelis has been involved to major cloud projects in Greece and abroad, helping companies to adopt and deploy cloud technologies, driving business value. He is entitled to a lot of Microsoft Expert Certifications, demonstrating his proven experience in delivering high quality solutions. He is an author, blogger and he is acting as a spokesperson for conferences, workshops and webinars. He is also an active member of several communities as a moderator in azureheads.gr and autoexec.gr. Follow him on Twitter @papostolidis.

