Azure Firewall is a virtual network firewall service that provides your resources in an Azure Virtual Network. It’s a firewall as a service, build on the cloud for the cloud. It provides both east-west and north-south traffic inspection. Some features are Threat Intelligence, DNAT, SNAT, Application & Network filtering rules, DNS Proxy, TLS Inspection, IDPS, URL Filtering, Web Categories. And as an Azure native service has built-in high availability and cloud scalability.
There is plenty of information and guides for Azure Firewall at the Microsoft Docs Azure Firewall documentation | Microsoft Docs. In this post, I want to share some PowerShell scripts that we created with my colleague Panagiotis Tsoukias. One script to Export all Firewall Policy rules, of all Policy Groups in a CSV file. Then edit the rules in Excel. And a second script to import the rules to the same or to a different Firewall Policy.
Export the Azure Firewall Policy Rules
The first script is to Export the Firewall Policy Rules of a Rule Collection, in a manageable CSV format. Edit the script, change the first three variables, and the path to export, and run it. Open the exported CSV with Microsoft Excel and you will have this result:
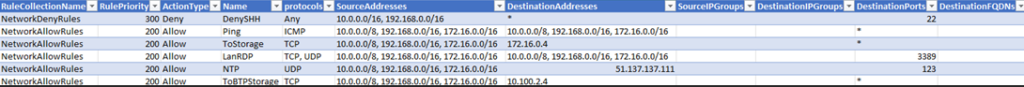
The first three columns are the Rule Collection’s Name, Priority & Action Type. We will need this info to create the Rule Collections and import the rules to the corresponding Rule Collection.
You can copy the script from the below box or download it from my GitHub link: Export Azure Firewall Policy Rules.ps1
#Provide Input. Firewall Policy Name, Firewall Policy Resource Group & Firewall Policy Rule Collection Group Name
$fpname = azfwpolicy
$fprg = azurehub
$fprcgname = DefaultNetworkRuleCollectionGroup
$fp = Get-AzFirewallPolicy -Name $fpname -ResourceGroupName $fprg
$rcg = Get-AzFirewallPolicyRuleCollectionGroup -Name $fprcgname -AzureFirewallPolicy $fp
$returnObj = @()
foreach ($rulecol in $rcg.Properties.RuleCollection) {
foreach ($rule in $rulecol.rules)
{
$properties = [ordered]@{
RuleCollectionName = $rulecol.Name;
RulePriority = $rulecol.Priority;
ActionType = $rulecol.Action.Type;
RUleConnectionType = $rulecol.RuleCollectionType;
Name = $rule.Name;
protocols = $rule.protocols -join ", ";
SourceAddresses = $rule.SourceAddresses -join ", ";
DestinationAddresses = $rule.DestinationAddresses -join ", ";
SourceIPGroups = $rule.SourceIPGroups -join ", ";
DestinationIPGroups = $rule.DestinationIPGroups -join ", ";
DestinationPorts = $rule.DestinationPorts -join ", ";
DestinationFQDNs = $rule.DestinationFQDNs -join ", ";
}
$obj = New-Object psobject -Property $properties
$returnObj += $obj
}
#change c:\temp to the path to export the CSV
$returnObj | Export-Csv c:\temp\rules.csv -NoTypeInformation
}
Import the Azure Firewall Policy Rules
After done editing the rules in Excel, we are ready to import them back to the Azure Policy or to a new Azure Policy. We need to export one CSV per Rule Collection. It will help us that the first column has the Rule Collection Name. Then run the import script. The script creates a Rule Collection, if it does not already exist, and adds the Rules in this specific Rule Collection.
You can copy the script from the below box or download it from my GitHub link: Import Azure Firewall Policy Rules.ps1
#Provide Input. Firewall Policy Name, Firewall Policy Resource Group & Firewall Policy Rule Collection Group Name
$fpname = azfwpolicy
$fprg = azurehub
$fprcgname = DefaultNetworkRuleCollectionGroup
$targetfp = Get-AzFirewallPolicy -Name $fpname -ResourceGroupName $fprg
$targetrcg = New-AzFirewallPolicyRuleCollectionGroup -Name $fprcgname -Priority 200 -FirewallPolicyObject $targetfp
$RulesfromCSV = @()
# Change the folder where the CSV is located
$readObj = import-csv C:\temp\rules.csv
foreach ($entry in $readObj)
{
$properties = [ordered]@{
RuleCollectionName = $entry.RuleCollectionName;
RulePriority = $entry.RulePriority;
ActionType = $entry.ActionType;
Name = $entry.Name;
protocols = $entry.protocols -split ", ";
SourceAddresses = $entry.SourceAddresses -split ", ";
DestinationAddresses = $entry.DestinationAddresses -split ", ";
SourceIPGroups = $entry.SourceIPGroups -split ", ";
DestinationIPGroups = $entry.DestinationIPGroups -split ", ";
DestinationPorts = $entry.DestinationPorts -split ", ";
DestinationFQDNs = $entry.DestinationFQDNs -split ", ";
}
$obj = New-Object psobject -Property $properties
$RulesfromCSV += $obj
}
$RulesfromCSV
Clear-Variable rules
$rules = @()
foreach ($entry in $RulesfromCSV)
{
$RuleParameter = @{
Name = $entry.Name;
Protocol = $entry.protocols
sourceAddress = $entry.SourceAddresses
DestinationAddress = $entry.DestinationAddresses
DestinationPort = $entry.DestinationPorts
}
$rule = New-AzFirewallPolicyNetworkRule @RuleParameter
$NetworkRuleCollection = @{
Name = $entry.RuleCollectionName
Priority = $entry.RulePriority
ActionType = $entry.ActionType
Rule = $rules += $rule
}
}
# Create a network rule collection
$NetworkRuleCategoryCollection = New-AzFirewallPolicyFilterRuleCollection @NetworkRuleCollection
# Deploy to created rule collection group
Set-AzFirewallPolicyRuleCollectionGroup -Name $targetrcg.Name -Priority 200 -RuleCollection $NetworkRuleCategoryCollection -FirewallPolicyObject $targetfp
Feel free to take, edit, use & comment on the scripts, you can find them at my repo:

Pantelis Apostolidis is a Sr. Specialist, Azure at Microsoft and a former Microsoft Azure MVP. For the last 20 years, Pantelis has been involved to major cloud projects in Greece and abroad, helping companies to adopt and deploy cloud technologies, driving business value. He is entitled to a lot of Microsoft Expert Certifications, demonstrating his proven experience in delivering high quality solutions. He is an author, blogger and he is acting as a spokesperson for conferences, workshops and webinars. He is also an active member of several communities as a moderator in azureheads.gr and autoexec.gr. Follow him on Twitter @papostolidis.


Very useful Pantelis! Thank you for sharing
It’s not working now. not getting full info. Can you update it with latest things and also make it working with all collection groups at onces?
Hi
i find your code. I have question.
This export ONLY DefaultNetworkRuleCollectionGroup.
If we have 10s on rule collection is there any way how to do this?
Unfortunately, only works with 1 Rule collection.
Script pastes all rules in 1 Rule collection.
I hope you can fix this, will be very useful.
This was very useful. I had to add the Connect-AzAccount and Set-AzContext to the beginning since we have multiple subscriptions.
I set the $fprcgname to my Rule Collection Group within my Policy and it extracted the rules without issue.
I have not tried the import function.
Thanks for sharing!
Thanks for this script. I went ahead and poorly modified it to work for url logs as i was getting errors. its not pretty, but it works.
#Provide Input. Firewall Policy Name, Firewall Policy Resource Group & Firewall Policy Rule Collection Group Name
$fpname = “policyname”
$fprg = “resourcegroupname”
$fprcgname = “DefaultApplicationRuleCollectionGroup”
$sub = “subscriptionname”
$file = “./urlrules.csv”
Connect-AzAccount
Set-AzContext -subscription $sub
$fp = Get-AzFirewallPolicy -Name $fpname -ResourceGroupName $fprg
$rcg = Get-AzFirewallPolicyRuleCollectionGroup -Name $fprcgname -AzureFirewallPolicy $fp
$returnObj = @()
foreach ($rulecol in $rcg.Properties.RuleCollection) {
foreach ($rule in $rulecol.rules)
{
$combined = $null
foreach ($protocol in $rule.protocols)
{
if ($combined -ne $null)
{
$combined = $combined += “,”
}
$combined = $combined += ForEach-Object { $protocol.ProtocolType + ‘:’ + $protocol.Port }
}
$properties = [ordered]@{
RuleCollectionName = $rulecol.Name;
RulePriority = $rulecol.Priority;
ActionType = $rulecol.Action.Type;
RUleConnectionType = $rulecol.RuleCollectionType;
Name = $rule.Name;
SourceAddresses = $rule.SourceAddresses -join “, “;
protocols = $combined;
TargetFqdns = $rule.TargetFqdns -join “, “;
TerminateTLS = $rule.TerminateTLS -join “, “;
}
$obj = New-Object psobject -Property $properties
$returnObj += $obj
}
#$returnObj
$returnObj | Export-Csv $file -NoTypeInformation
}
Thank you so much for sharing Larry!